Are Encrypted Lockboxes for Data Centers Worth the Usability Cost? | Data Center Knowledge | News and analysis for the data center industry

Info Security Products Guide Names Black Box EncrypTight a Silver Award Winner for its 2013 Global Excellence Awards | Business Wire

Vintage encryption and data security concept with combination puzzle box or Cryptex with secret message inside | Office of the CTO Blog
GitHub - NEARFoundation/near-js-encryption-box: An experimental library to encrypt and decrypt data using the NEAR account's ed25519 keypairs







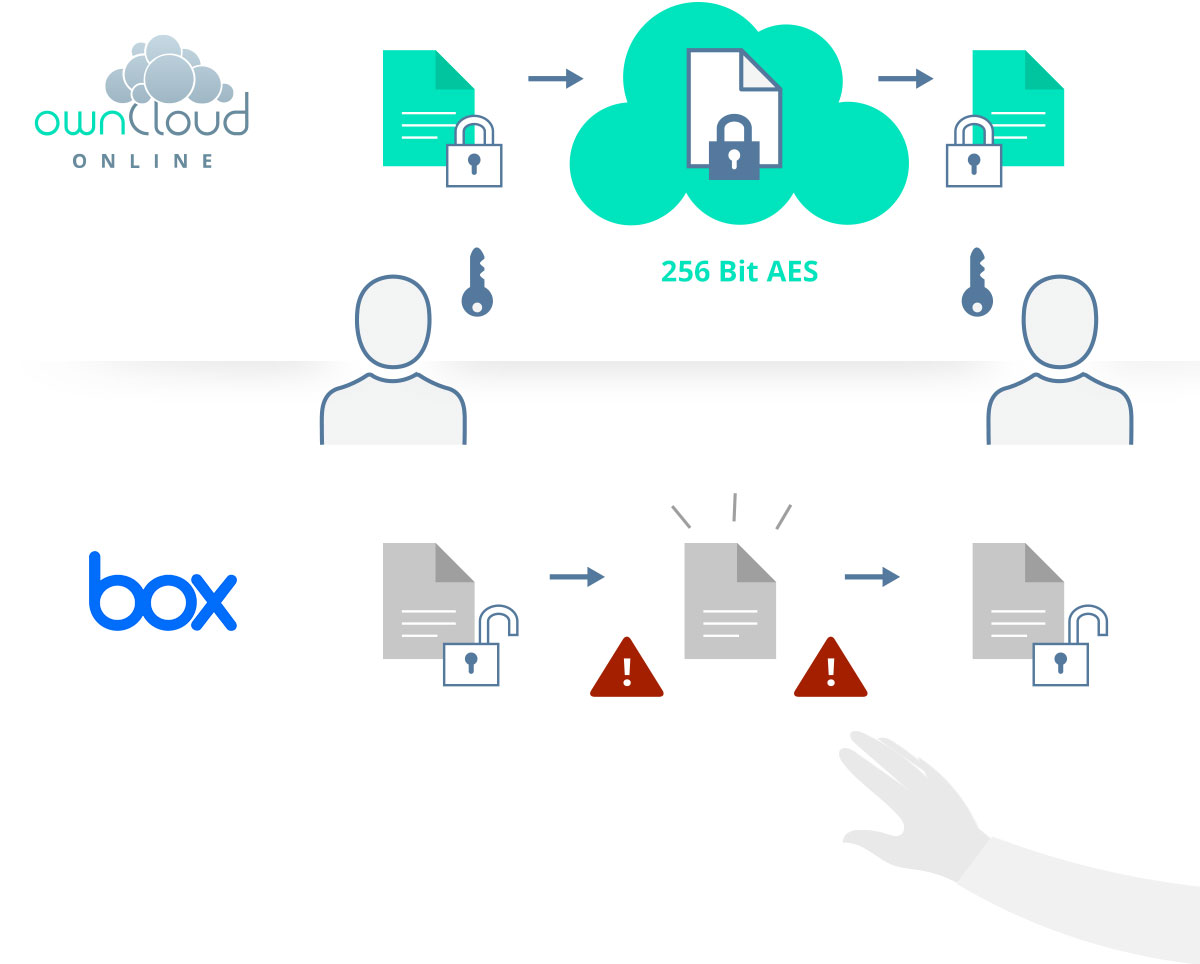


/cdn.vox-cdn.com/uploads/chorus_asset/file/3395694/Box_EKM_Encryption_Flow.0.png)